I have a Mac To disable the Firewall on your Mac: Right-click the McAfee M icon in the menu bar. Click (product name) Console. For example, LiveSafe Console. Click Mac Security, or click the gear icon at the top-right corner. Click the lock to make changes, then type your password. Click the slider to turn off the Firewall. Apr 07, 2016 If you use a Mac, chances are you might not even realize that OS X comes with a firewall. This firewall helps ensure unauthorized app and services can’t contact your computer, and prevents intruders from sniffing out your Mac on a network.
Updated: January 3, 2020 Home » Computer and Internet Security » Download Free Antivirus [ Windows / macOS ]
ZoneAlarm Free Firewall. Mac OS X Firewall. If you’re reading this from a computer running Mac OS X 10.5 or later, the built-in firewall is robust and somewhat customizable, and it just. ZoneAlarm Free Firewall retains its title as Editors' Choice for free personal firewall. Free Antivirus 2018 License key + Activation Code For Windows + MAC services and products Free Antivirus 2018 License key + Activation Code For Windows + MAC is a household that of security applications developed by Avast Software for Microsoft. Sophos Firewall Home Edition. Give your home network a much needed security boost. The Home Edition of the Sophos Firewall features full protection for your home network, including anti-malware, web security and URL filtering, application control, IPS, traffic shaping, VPN, reporting and monitoring, and much more.
One of the biggest myth regarding computer security on an Apple Mac is your computer will never ever be infected with any malware. Due to the fact that most Apple Mac OS X user does not have any antivirus installed, let alone any fire wall, it becomes hackers favorite target. Firewall for Mac is good for Stopping spyware, Monitoring any keylogger installed and Stop Trojan from sending credit card information.
Alternative 2020 Article ➤ 21 Complete List Comparison Of macOSX Antivirus Apps
↓ 01 – One Periodic’s Hands Off! | $49.99
To keep you and your computer secure, Hands Off! silently monitors all operations performed by the applications running on your computer. As soon as an application tries to perform an operation for which there is no rule defined, a Hands Off! notification will appear. The notification contains all the relevant information about the operation to allow you to make an informed decision. Moreover, until you answer the notification, the operation is safely blocked and Hands Off! keeps you protected.
- Prevents applications from phoning home
- Blocks outgoing network connections
- Blocks incoming network connections
- Blocks domain name resolving
- Easily blocks multiple subdomains
- Protects from trojans, worms and network parasites
- Supports IPv4, IPv6 and local networks
↓ 02 – Little Snitch 3 | Network Monitoring | € 29.95
Firewall for incoming connections. Little Snitch not only reveals any outgoing network connection attempt to make sure that sensitive data doesn’t leave your computer without your consent. The inbound firewall in Little Snitch provides you with the same level of control for incoming connections.
↓ 03 – Murus Lite App | OS X Firewall Unchained | FREE
Murus Lite is the entry level firewall front end. Everybody can download it and use it for free. It features inbound filtering and logging and can be used to protect services running on the Mac. Despite being free Murus Lite is not a tryout or demo. It is a full featured app and is a good starting point for the novice user.
- Inbound filtering
- Inbound logging
- Expanded PF Config.
- Ports Management
Free Firewall For Windows 10
The Firewall For Mac Catalina
↓ 04 – Radio Silence | Firewall For Mac | USD9
Radio Silence is a tiny firewall that lets you block any application from accessing the internet. It is designed for people who are not interested in configuring traditional firewalls. Radio Silence supports OS X Yosemite, Mavericks, Mountain Lion, Lion, and Snow Leopard. It only takes a few seconds to install.
The Firewall For Mac Windows 10

- 100% Annoyance-free – Radio Silence respects your concentration. That is why it will never interrupt you with pop-up windows or alerts.
- Zero Maintenance – Once the firewall is installed, you can forget all about it. It is always on and needs no attention from you.
- Tiny and Fast – Radio Silence weighs next to nothing. It doesn’t waste any time or resources, which also makes it blazingly fast.
- Usable by Anyone – You don’t have to be a network expert to use this firewall. It takes care of all the technical details for you.
How to Turn on Firewall Security on Apple Mac OS

The Mac firewall is turned off by default, no reason given by Apple why they did not enabled it by default. It is always better to be safe than sorry, therefore there is nothing to lose by enabling it, especially if your router has no Hardware Firewall capability.
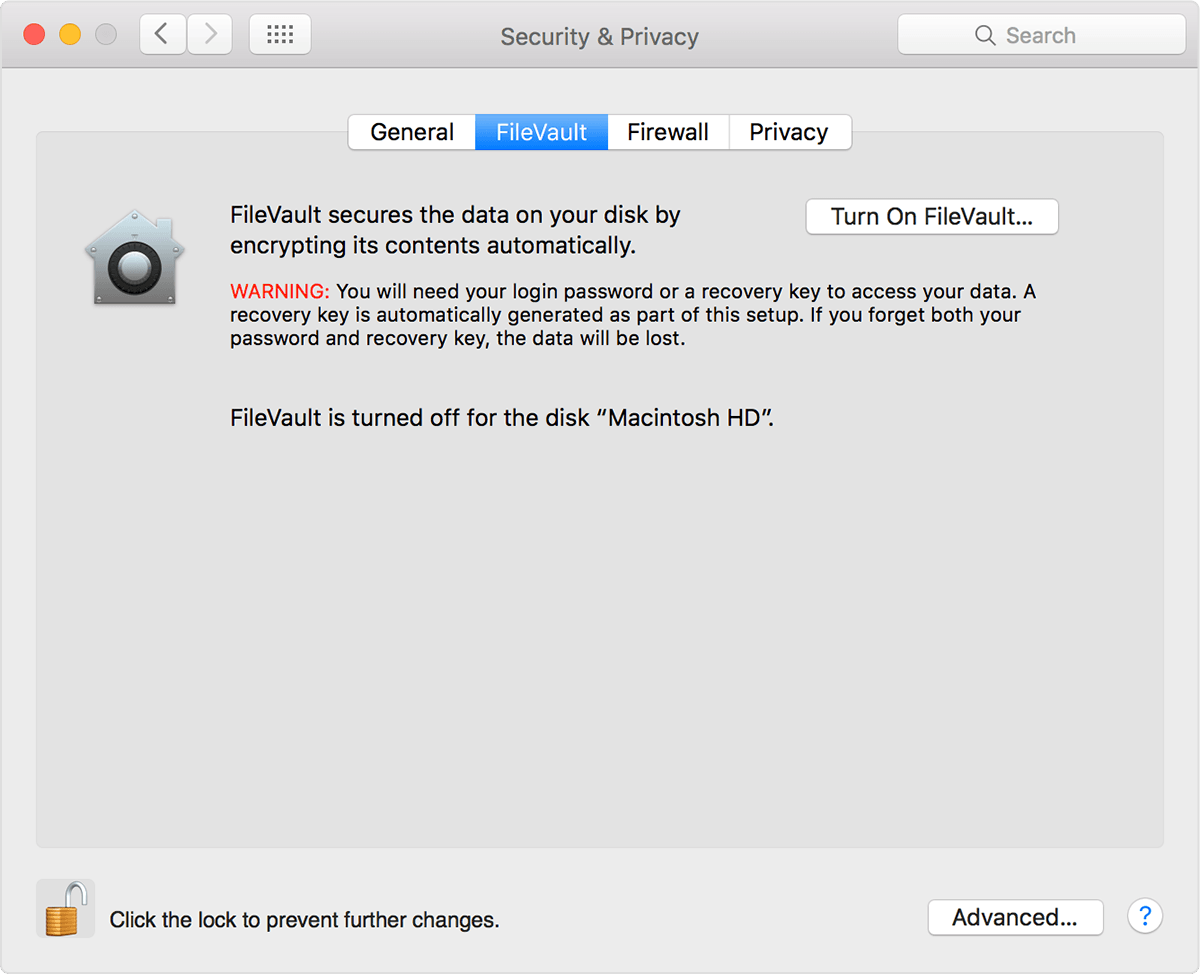
Step 1 – Go to ‘System Preferences‘, click on ‘Security & Privacy‘.
Step 2 – On the Security & Privacy window, click on the ‘Firewall‘ tab.
Step 3 – To turn on the firewall security feature, you will need to unlock it. To unlock this settings window click on the padlock in the bottom left corner of the window. Set the password to unlock it.
Step 4 – With the Firewall feature unlocked, click on the ‘Turn On Firewall’ button. Congratulation, the firewall on the Apple Mac OS X is now enabled.
Mac Computers Fall Prey to Flashback Trojan
With the ever-growing volume of malicious software attacks on Mac computers, Mac users no longer feel their computers are safe from Internet security risks. The Flashback Trojan virus has affected over 700,000 users. Find out if your Mac is infected – and discover how to protect against Flashback and Mac OS X malware attacks.
Firewall For Mac
What Is The Firewall For Mac
- Taking care of the entry of credit card data from customers, in a way that sensitive card details are gathered and transmitted securely
- Secured data storage, which is outlined in the 12 security domains of the PCI standard, such as encryption, ongoing monitoring, as well as security testing of access to card data
- Annual validation of the required security controls, which can involve forms, questionnaires, external vulnerability scanning services, and 3rd party audits
Although the PCI SSC has no legal authority to compel compliance, not only is it a strict requirement for any company that processes credit or debit card transactions but PCI certification is also considered the best way to protect sensitive data and information, which further help businesses build and fortify long-lasting and trusting relationships with their customers.
PCI DSS certification

A successful data breach that exposes sensitive customer information can have severe repercussions on an organization. This may include fines from payment card issuers, lawsuits, loss of profits and a heavily damaged reputation. Not only that but the company may also have to cease accepting credit card transactions or be forced to pay higher subsequent charges than the initial cost of security compliance. That said, the investment in PCI security procedures proves to go a very long way in ensuring that other aspects of a business are safeguarded from cybercriminals.
PCI certification ensures the protection of card data through a set of requirements implemented by the PCI SSC. These include a few commonly known best practices, such as installation and use of free antivirus and firewall like Comodo Internet Security (CIS), as well as the encryption of data transmissions. What's more, companies must also restrict ingress to cardholder data and monitor access to network resources.
PCI DSS adherence
Take a closer look at the six main requirements of the PCI standard and some tips on how you can successfully abide by them.
Building and maintaining a secure network
Apart from installing and maintaining free antivirus and firewall configuration to protect cardholder data, your company should also come up with its own firewall configuration policy and develop a configuration test procedure.
System passwords and other security parameters should not come from vendor-supplied defaults. This means creating, preserving and updating your system passwords with unique and secure combinations, instead of something that a software vendor might already have in place upon purchase.
Protecting cardholder data
A PCI-compliant hosting provider should deliver multiple layers of defense and a secure data protection model, which integrates physical and virtual security methods for companies that store cardholder data.
Your company should also encrypt the transmission of cardholder data across open, public networks. As an added security measure, sensitive authentication data, such as card validation codes or PIN numbers, must never be stored after authorization, even if they're already encrypted.
Maintaining a vulnerability management program
Your free antivirus and firewall need to be frequently updated to protect against the most recently developed malware. Furthermore, keep on developing and maintaining secure systems and applications, which includes discovering newly identified security vulnerabilities via alert systems.
Carrying out strong access control measures
Restrict access to cardholder data by business need-to-know. Capping the number of personnel that has a way into cardholder data will minimize the chances of a security breach.
Designate a unique ID to each person with computer access as well. They should follow best practices, such as password encryption, authorization, authentication, password updates every 30 days, log-in time limits, and more.
If your data is hosted in an off-site data center, on the other hand, your data center provider should have limited personnel with access to sensitive information. PCI-compliant data centers should have full monitoring, as well as surveillance cameras and entry authentication to ensure a secure environment.
Tracking and monitoring entry to network resources and cardholder data
Take advantage of logging systems, which can track user activity and stored archives to help your hosting provider identify the cause in the event of a security breach or other concerns.
Firewall For Mac
Test security systems and processes habitually to ensure that your customers' cardholder data is safe at all times.
The cost of noncompliance, both in monetary and reputational terms, should be enough to persuade any business owner to take data security seriously. As such, consider using Comodo Internet Security to guard your system against dangerous viruses and other malwares. We make sure to secure business-oriented data to prevent security breaches from occurring.
Mac Os X Firewall
Related Resource